Why Secure by Design for IoT?
IoT devices are increasingly vulnerable to cyber threats, emphasizing the need for robust security from design to deployment. Without proper security measures, the consequences of vulnerable IoT devices can be severe:
- Data Breaches: Vulnerable IoT devices can lead to unauthorized access and leakage of sensitive user data.
- Zombie Army: Insecure IoT devices are often targeted for inclusion in botnets, which can launch large-scale distributed denial-of-service (DDoS) attacks.
- Physical Safety: Malicious actors can exploit vulnerabilities in IoT devices to manipulate critical systems.
Secure functionalities such as cloud service authentication, secure network communication, and secure Over-the-Air (OTA) updates must be prioritized from the ideation phase through to production. This proactive approach is crucial for mitigating risks, costs and safeguarding both users and organizations.
NXP i.MX SoCs: Powering Secure IoT Devices
The i.MX family offers low-power ARM-based processors ideal for multimedia applications. These System-on-Chip (SoC) devices integrate various processing units, including a CPU, video processing unit, and graphics card.
Starting with the i.MX6 series, these SoCs boast a well-supported High Assurance Boot (HAB) feature. HAB unlocks numerous security features, enhancing Bill of Materials (BOM) efficiency and boosting security throughout your design process.
Building a Chain of Trust (CoT): The Foundation of Security
A Chain of Trust (CoT) safeguards your IoT product from various threats like IP theft, unauthorized access, and hijacking. It ensures the integrity and tamper-proof nature of your system.
i.MX SoCs leverage HAB to establish a CoT. This CoT verifies the authenticity of every software component (bootloader, kernel, device tree and intellectual property (IP)) through hardware OEM locks and signature checks. This secure environment enables the use of OP-TEE Trusted Applications (TAs) to create a software-based Trusted Platform Module (fTPM) accessible via PKCS#11 from a Secure World.
Why Use PKCS#11?
PKCS#11 (Public Key Cryptography Standards #11) is a widely supported open-source project that facilitates secure cryptographic operations. It provides a standardized interface for accessing cryptographic tokens such as TPMs (Trusted Platform Modules) and HSMs (Hardware Security Modules).
In environments without PKCS#11 support, cryptographic keys are often stored directly on devices or in software, making them vulnerable to unauthorized access or compromise. PKCS#11 addresses this issue by abstracting cryptographic operations and securely managing keys within hardware tokens. This ensures that sensitive keys are protected from exposure, reducing the risk of data breaches and ensuring compliance with security standards.
Leading IoT cloud platforms like AWS and Azure utilize PKCS#11 to facilitate device authentication and secure cloud connections without exposing secret keys to the cloud infrastructure. Similarly, OTA (Over-The-Air) update clients such as SWUpdate and Mender leverage PKCS#11 to securely manage cryptographic keys used in the update process, safeguarding against tampering and unauthorized access.
By adopting PKCS#11, organizations can enhance the security of their IoT and cloud deployments, ensuring robust protection of sensitive cryptographic assets and maintaining compliance with industry security standards.
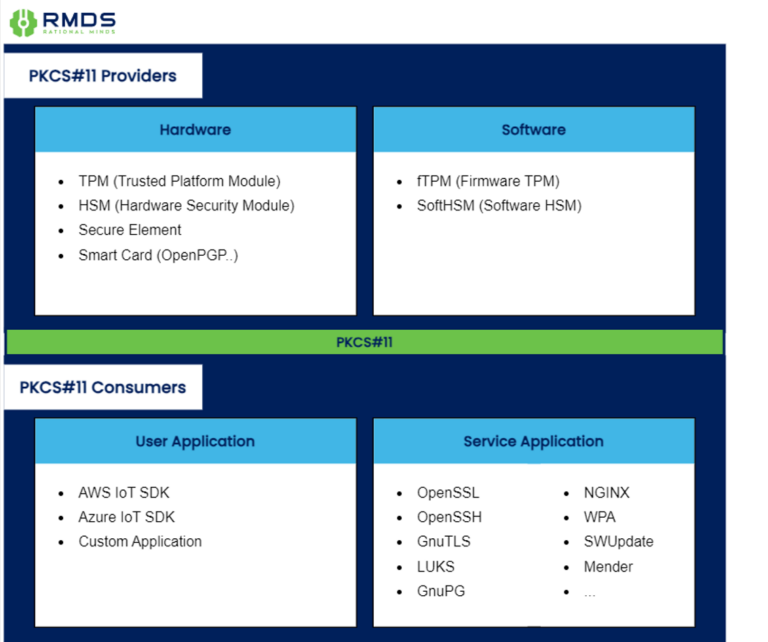
Key Management in NXP IoT Devices
Unlike user-based devices, IoT devices rely on keys and certificates for authentication and secure communication. PKCS#11 enables providers to act as keystores, supporting secure cryptographic operations without exposing private keys to end-users.
i.MX processors (from the i.MX6 series onwards) provide a range of security features to implement an fTPM as a PKCS#11 provider. This functionality combines ARM TrustZone technology with an open-source Secure OS like OP-TEE to achieve functionalities similar to HSMs/TPMs/Secure Elements. OP-TEE OS can run various TAs, including an fTPM, for diverse purposes.
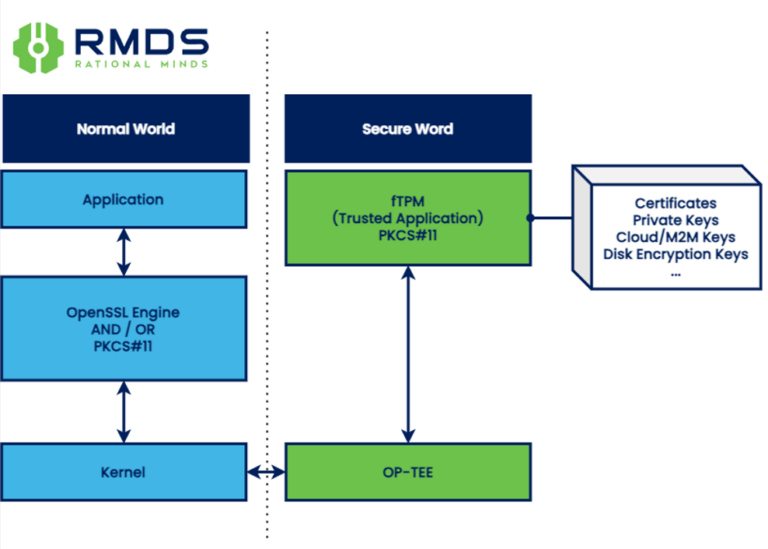
Important Notes :
- A secure OP-TEE requires a pre-established CoT for security (e.g., Secure Boot)
- A secure OP-TEE necessitates SoC-supported HUK (Hardware Unique Key) (e.g., NXP i.MX with CAAM or EdgeLock) for secure storage.
Supply Chain Key Management Challenges
Creating a secure CoT for your IoT solutions requires careful consideration throughout the development process. Implementing Secure Boot on NXP i.MX SoCs involves a Public Key Infrastructure (PKI) tree with four private keys that must be kept confidential. NXP i.MX Secure Boot is a one-time programmable option. If compromised, your entire device fleet becomes vulnerable.
Implementing secure key management within the supply chain is another crucial aspect. Using an HSM as a PKCS#11 provider offers a secure keystore with physical, network, and hardware security for your CoT. Keys and certificates reside within a secure element, preventing private key exposure.
Yocto Project: Streamlining Secure Development
The Yocto Project, combined with the NXP Code Signing Tool, facilitates filesystem key signing during the Yocto build process. At Rational Minds, we have implemented a layer that leverages PKCS#11 support within the Yocto solution. This allows for integrating security features within the supply chain and seamlessly fits with continuous integration/development (CI/CD) workflows by enabling Yocto builds to sign all necessary components. Ultimately, PKCS#11, along with PKCS#11-Proxy, empowers tools like GitLab Runner to utilize a shared HSM within your private network or secure connection.
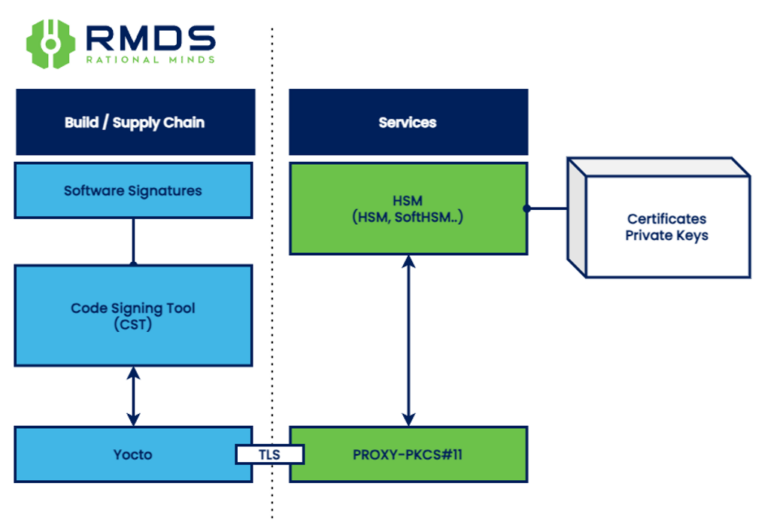
Conclusion
Leveraging OP-TEE as a PKCS#11 provider strengthens your IoT device security and eliminates the need for dedicated security chips, reducing BOM costs. Additionally, using an HSM as a PKCS#11 provider for your supply chain fulfills the minimal security requirements for managing keys across different teams, services, and systems.
Rational Minds offers different layers to meet PKCS#11 and HSM requirements inside a Yocto solution by leveraging NXP i.MX security features and applications. Schedule a free security consultation with us to learn more.

Walter Bonetti
Senior Software Developer
