This article addresses the importance of robust security for IoT devices and offers guidance on achieving it using the PKCS#11 standard with Python libraries like azure-iot-sdk-python, paho-mqtt, PyOpenSSL. While the official azure-iot-sdk-python library currently lacks built-in PKCS#11 support, we’ll explore alternative approaches to safeguard your devices and X.509 credentials.
Why PKCS#11 Matters for IoT Security
The PKCS#11 (Public Key Cryptography Standards #11) interface provides a standardized way to interact with Hardware Security Modules (HSMs) and Trusted Platform Modules (TPMs). This dedicated security hardware offers significant advantages over storing private keys directly on the devices:
- Enhanced Security: HSMs and TPMs isolate cryptographic operations within a tamper-resistant environment, minimizing the risk of private key compromise.
- Simplified Management: PKCS#11 provides a consistent interface for managing cryptographic keys across different HSM/TPM vendors.
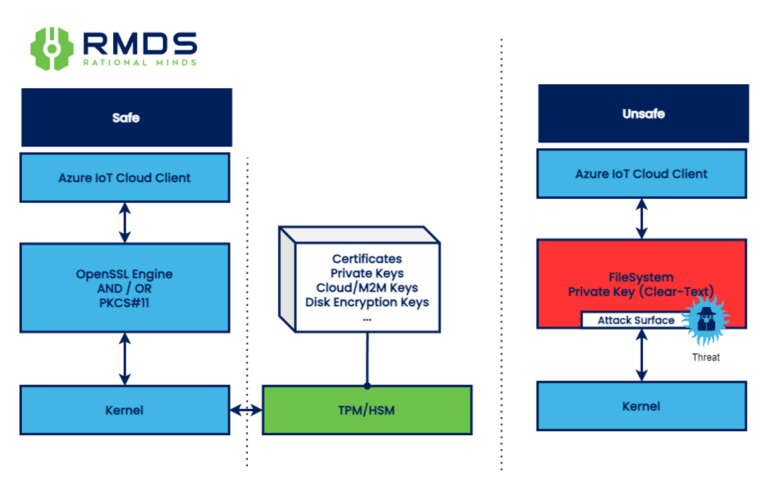
Identifying Your Security Posture
To assess your current security posture, consider these questions:
- Does my product leverage azure-iot-sdk-python with custom PKCS#11 support?
- Yes: Your private keys are likely protected from direct exposure.
- No: Your product might be vulnerable to private key theft.
- Does my product use PKCS#11 with the Azure IoT Hub client?
- Yes: Your private keys are likely protected.
- No: Your product might be vulnerable.
Alternative Approaches for Securing Azure IoT Hub Clients
While azure-iot-sdk-python lacks native PKCS#11 support, here are alternative strategies to secure your connection:
- Custom Azure MQTT Python Client with PyOpenSSL Context (Fork):
- Use an alternative programming language such as C:
- See Microsoft Documentation: Provision Devices with X.509 for more information.
Steps to Secure Your Azure IoT Device
Here’s a roadmap to implement PKCS#11 support for your Azure IoT device:
- Enable PKCS#11 Engine:
- Configure your TPM or fTPM in the /etc/ssl/openssl.cnf file to activate the OpenSSL PKCS#11 engine.
- Provision X.509 Credentials:
- Use pkcs11-tool to provision your TPM with X.509 credentials obtained from your provisioning process (or existing devices if already deployed).
- Create Custom PyOpenSSL Context:
- Develop a custom PyOpenSSL context that utilizes the PKCS#11 identity engine.
- Test the Connection:
- Establish a secure connection between your device and your Azure IoT Hub to validate the integration.
- X.509 Handling in Production:
- If already in production, import the X.509 credentials (step 4) and remove the private key from the system to prevent unauthorized access.
Conclusion
This article provided a foundational approach for securing Azure IoT devices using PKCS#11 with Python libraries. While the current solution might require further tailoring, it paves the way for enhanced security.
For more comprehensive solutions and supply chain/edge device integration, consider exploring Rational Minds suite of services. Schedule a complimentary security consultation to discuss your specific requirements.
